Manage Open Liberty with Admin Center
The Admin Center is a web-based graphical user interface (GUI) for Open Liberty servers. You can use the Admin Center to manage your server configuration, OpenID Connect permissions, and Java batch jobs.
Set up Admin Center
If the Admin Center feature is not already installed in your runtime, install it by running the featureUtility installFeature command from the
path_to_liberty/wlp/bindirectory, as shown in the following example.Copied to clipboardfeatureUtility installFeature adminCenter-1.0Enable the Admin Center feature in your
server.xmlfile and configure a management role for either the reader or administrator role.Admin Center is only accessible over HTTPS, you must specify an HTTPS port and configure a keystore to protect
keystorefiles that contain server authentication credentials. You can use the following exampleserver.xmlfile to set up a test instance of Admin Center.
This example enables the adminCenter-1.0 feature and configures a basic user registry that defines users in the reader-role and administrator-role management roles. It also specifies an HTTPS port in the httpEndpoint element and a default keystore and password reference in the keyStore element.
<server description="Admin Center example server">
<featureManager>
<feature>adminCenter-1.0</feature>
</featureManager>
<basicRegistry id="basic">
<user name="admin" password="adminpwd" />
<user name="reader" password="readerpwd" />
</basicRegistry>
<administrator-role>
<user>admin</user>
</administrator-role>
<reader-role>
<user>reader</user>
</reader-role>
<keyStore id="defaultKeyStore" password="Liberty" />
<httpEndpoint id="defaultHttpEndpoint"
host="*"
httpPort="9080"
httpsPort="9443" />
</server>Log in to Admin Center
Before you access the Admin Center GUI, make sure that your server is running. In a web browser, go to the Admin Center login page at the following URL.
https://host_name:port_number/adminCenter
For the host_name value, specify the IP address or domain name server (DNS) hostname of the computer that the Open Liberty server runs on. If the browser is running on the same computer as the server, you can specify localhost as the hostname. For the port_number value, specify the httpsPort value from the httpEndpoint element in your server.xml file.
For example, if your browser is running on the same computer as your server and you use the previous example server.xml configuration, Admin Center is accessible from the following URL.
Access to Admin Center is supported only when the access comes directly from a browser. Access through an HTTP proxy server is not supported.
If your browser prompts you to confirm that the connection is trusted, specify an exception or otherwise enable the connection to continue to Admin Center. To log in to Admin Center, specify the username and password from your management role configuration. For example, if you use the previously provided example server.xml configuration, specify admin as the username and adminpwd as the password.
The following screen capture shows the Admin Center login screen.
Select tools from the Toolbox
After you log in to Admin Center, the browser displays the Toolbox, which contains tools such as the Server Config and Explore tools and a bookmark to the Open Liberty website.
The following screen capture shows the Admin Center Toolbox.

The Server Config and Explore tools are available by default. The Java Batch and OpenID Connect tools are available only if you enable and configure the respective Open Liberty features for those functions. You can add or remove tools from the Toolbox by selecting the Edit icon. To use a tool, select its Toolbox icon.
The following tools are available from the Admin Center.
Manage and test your server configuration with the Server Config tool
You can use the Server Config tool to view and edit Open Liberty server configuration files and to test server connections to different resources. To edit configuration files or test connections, you must be in the administrator-role management role.
Before you can edit configuration files, the tool prompts you to add a remoteFileAccess element to your server.xml file. You can copy the example element from the browser window or configure it manually. If you do not add this element, the configuration files are shown in read-only mode.
To enable write access to configuration files, add the following code to your server.xml file.
<remoteFileAccess>
<writeDir>${server.config.dir}</writeDir>
</remoteFileAccess>The Server Config tool displays configuration files, such as a server.xml file, in two modes: Design and Source. Each of these modes can be accessed from a browser tab within the tool. You can customize these modes by clicking the Settings icon. For example, you can add or remove parameter descriptions in Design mode or add or remove line numbers in Source mode.
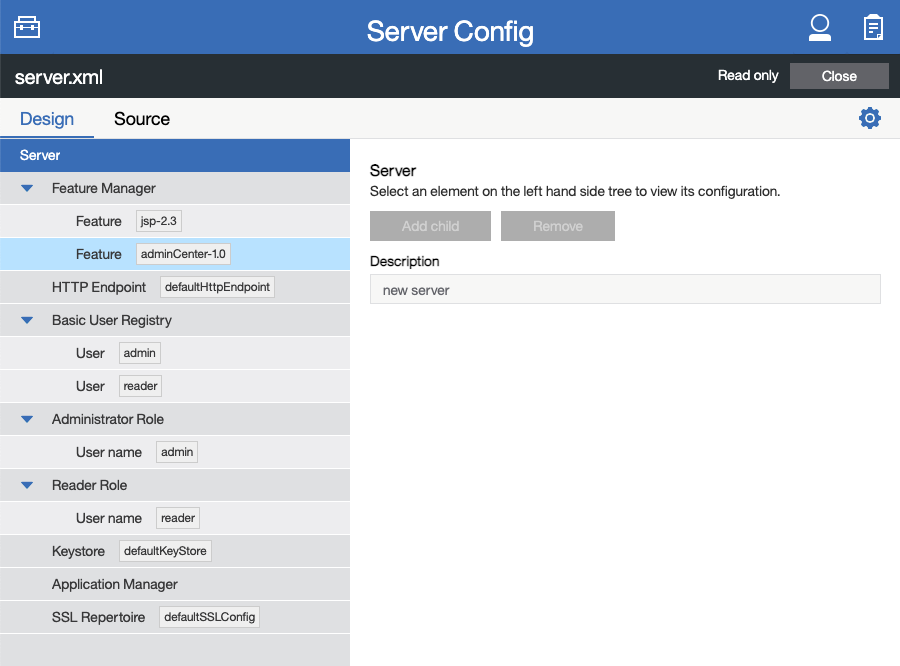
The Design mode displays the content of configuration files by using graphical controls with inline documentation. In this mode, select elements in the configuration to see enabled features and parameter settings.
The Source mode enables direct access to edit the file text and provides tooltip descriptions for file elements. Hover over elements and parameters to view their documentation. You can press Ctrl+Space to use content assist, which helps you add new elements, parameters, and values. However, the Source mode editor does not validate the configuration values that you specify. Changes that you make in Source mode are applied to your running server. Specifying invalid configuration values might produce errors or cause your server to fail.
The following screen capture shows the Design tab of the Server Config tool.
Test server connections to resources with the Server Config tool
You can test the connection to Java Database Connectivity (JDBC), Java EE Connector Architecture (JCA), Java Message Service (JMS), and Cloudant resources by using the Server Config tool.
To test connections with the Server Config tool, you must enable the Admin REST Connector and MicroProfile OpenAPI features in your
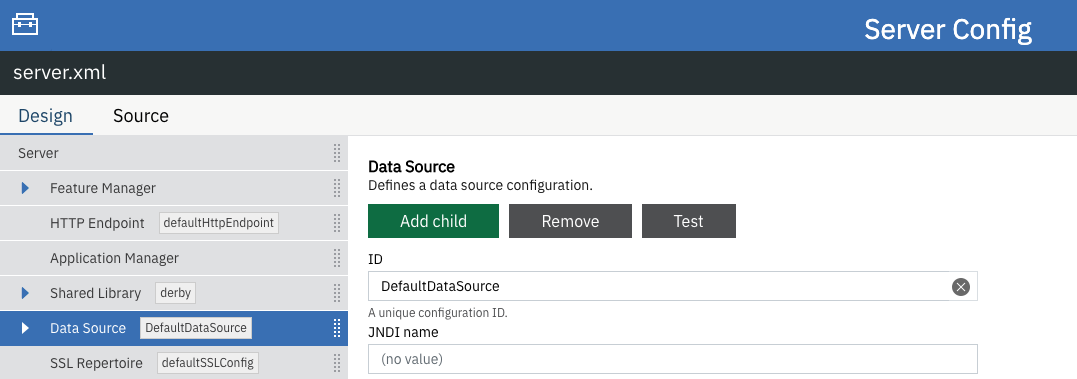
server.xmlfile, in addition to the Admin Center feature. You must also enable any features to support the server resource that your are checking the connection to. The following example also enables the JDBC feature to support a database connection.Copied to clipboard<featureManager> <feature>adminCenter-1.0</feature> <feature>restConnector-2.0</feature> <feature>mpOpenApi-3.0</feature> <feature>jdbc-4.3</feature> ... </featureManager>In the Server Config tool, select the resource for which you want to test the connection from the Server menu in the Design tab.
In the display window for your chosen resource, click the Test button.
The following screen capture shows the Design tab and the display window for the chosen resource in the Server Config tool.
Choose the authentication method that you want to employ for the connection test. The three authentication methods are: Container authentication, Application authentication, or No resource reference.
The following screen capture shows the Connection Test page and the authentication methods.
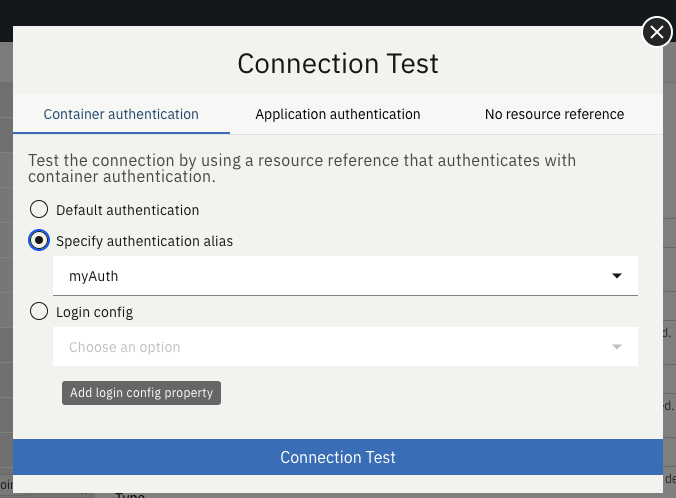
In the selected authentication method, specify the required fields and click the Connection Test button. The result of the test is displayed.
The Admin Center uses REST APIs to validate the connections. For more information, see Validating server connections.
Monitor and manage resources with the Explore tool
You can use the Explore tool to monitor and manage Open Liberty resources. This tool offers options to view information about the server and its applications. You can also use it to stop, start, or restart resources.
For more timely updates to server and application status in the Explore tool, add the Web Socket feature to your server configuration. This feature provides a live view of the topology, regardless of size. Without the Web Socket feature, Admin Center periodically and frequently polls for changes.
You can select the Applications view from the navigation bar to monitor, stop, start, or restart applications that are running on your server.
The Monitor view on the navigation bar shows server and system metrics graphically in charts. You can use the Monitor view to track heap memory, loaded classes, active Java virtual machine (JVM) threads, and central processing unit (CPU) usage.
The following screen capture shows the Monitor view of the Explore tool.
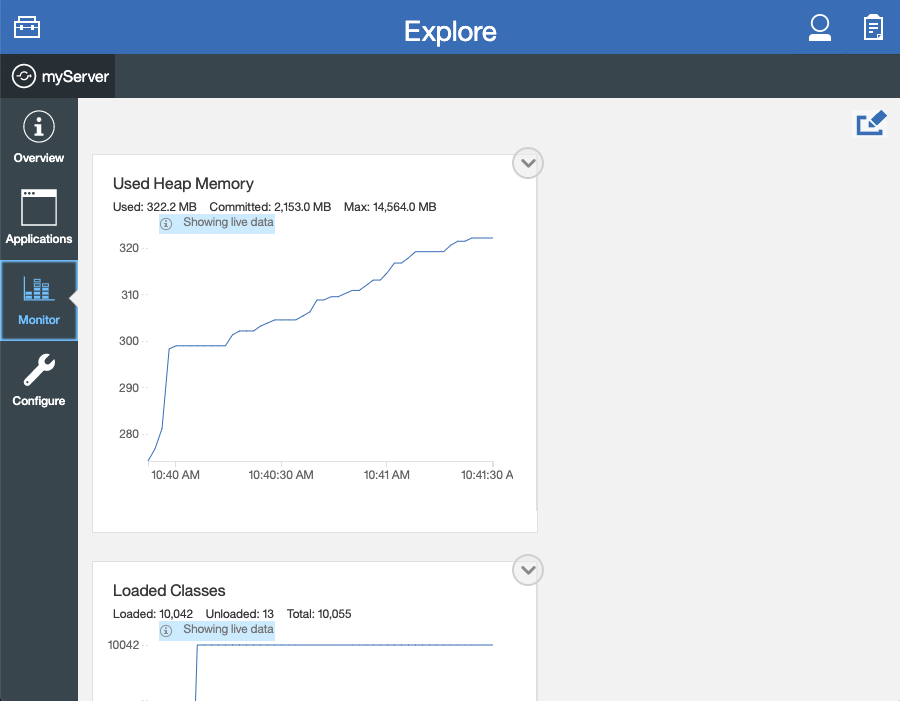
You can add more resource metrics to the Monitor view by selecting the Edit icon and choosing an option from the menu. When the Performance Monitoring feature is enabled, more resource metrics are available from this menu. Depending on what resources are configured for the server, the following resource metrics might be available:
Active Sessions
Active Liberty Threads
Average Response Time
Average Wait Time
Request Count
Used Connections
Manage Java batch jobs with the Java Batch tool
If you configure the Batch Management feature, you can access the Java Batch tool. With this tool, you can view the progress and status of your Java batch jobs, manage their instances, and view their log files.
The following screen capture shows the Java Batch tool.
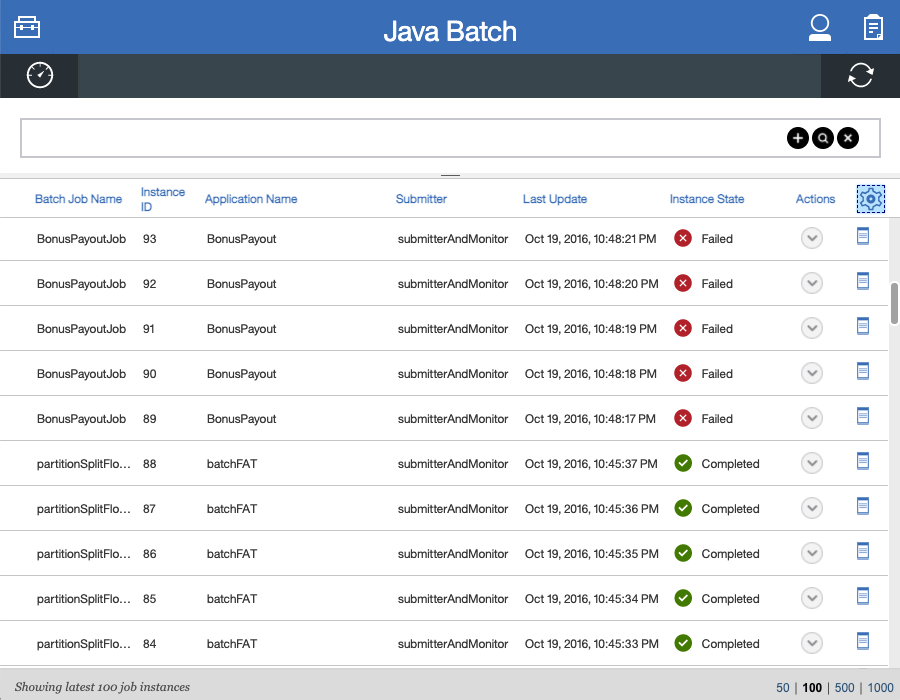
Each batch job has an Actions icon, which you can select to stop, restart, or purge the job, and a View Logs icon, which you can select to view the job logs. To view details and metrics for a batch job, hover over the Batch Job Name and select an option from the tooltip menu.
If batch jobs or job logs are on remote servers, configure cross origin region sharing (CORS) on each remote server. CORS enables Admin Center to request job information from remote servers.
The Batch Management feature requires custom authorization to view and manage batch jobs. To use the Java Batch tool, you must configure a com.ibm.ws.batch custom authorization role, in addition to the reader or administrator management role that is required to access the Admin Center. The following server.xml file example shows configuration for a wanda user who is granted the administrator management role and the batchAdmin custom authorization role.
<administrator-role>
<user>wanda</user>
</administrator-role>
<authorization-roles id="com.ibm.ws.batch">
<security-role name="batchAdmin">
<user name="wanda"/>
</security-role>
</authorization-roles>With this configuration, the user has authorization to view and manage any configured Java batch jobs.
A com.ibm.ws.batch custom authorization role can also be combined with the reader management role. This combination still allows full access to the Java Batch tool but provides read-only access to other Admin Center resources.
However, if no custom batch authorization role is configured, even a user in the administrator management role cannot view or manage Java batch jobs.
Administer OpenID Connect Provider tasks with the OpenID Connect (OIDC) tools
If you enable the OpenID Connect Provider feature and configure OpenID Connect, you can access the following OpenID Connect tools from the Admin Center:
- OpenID Connect Client Management
You can use this tool to allow an administrator to manage clients on an OIDC provider.
- OpenID Connect Personal Token Management
You can use this tool to allow a user to manage application passwords and application tokens on an OIDC provider.
- OpenID Connect Users Token Management
You can use this tool to allow an administrator to revoke application passwords and application tokens of other users on an OIDC provider.
For more information, see Admin Center OpenID Connect tools.




